Your Port scanning attack examples images are ready. Port scanning attack examples are a topic that is being searched for and liked by netizens now. You can Get the Port scanning attack examples files here. Get all royalty-free images.
If you’re searching for port scanning attack examples images information related to the port scanning attack examples interest, you have pay a visit to the ideal blog. Our website always gives you hints for seeing the maximum quality video and picture content, please kindly surf and find more enlightening video content and images that match your interests.
Port Scanning Attack Examples. A closed response means the port is inactive not listening and not responding. Network scanning and port scanningprocesses for learning about a networks structure and behaviorarent inherently hostile but bad actors often use them to conduct reconnaissance before trying to breach a network. Businesses also require strong security software port scanning tools and security alerts that monitor ports and prevent malicious actors from reaching their network. The idea is to probe as many listeners as possible and keep track of the ones that are.
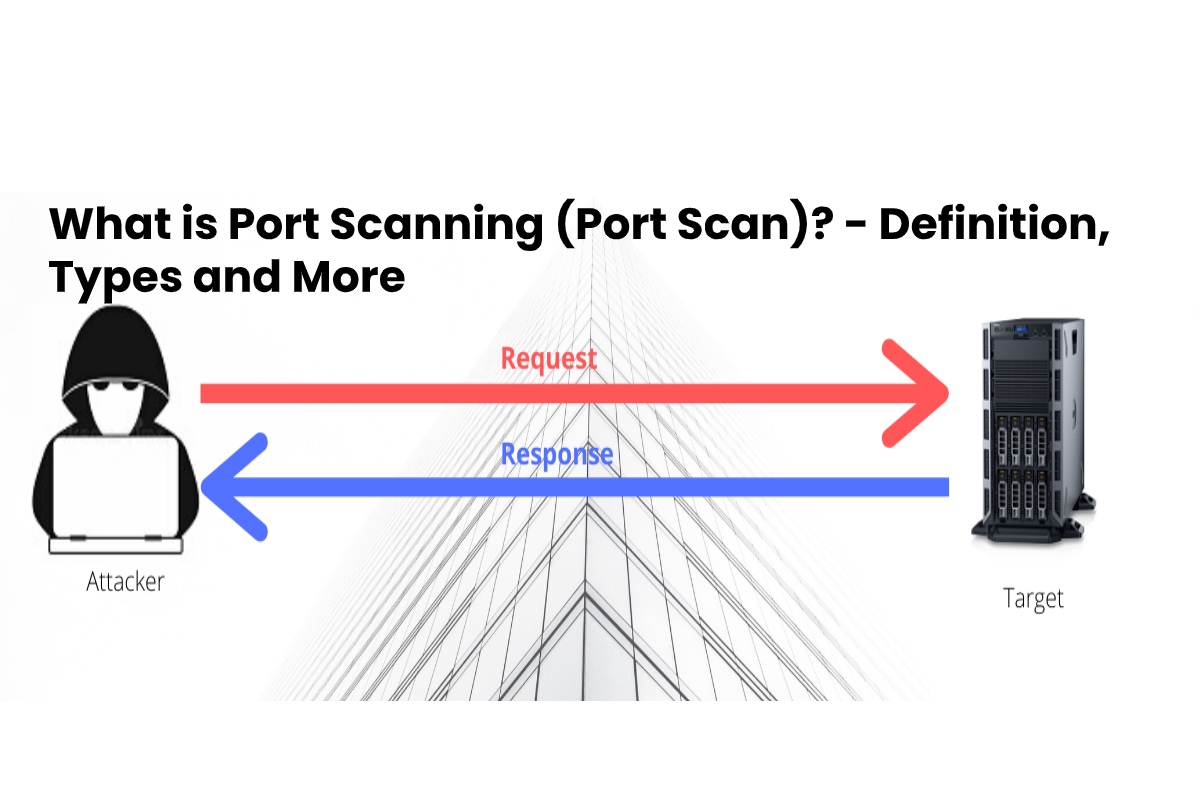 What Is Port Scanning Port Scan Definition Types And More From computertechreviews.com
What Is Port Scanning Port Scan Definition Types And More From computertechreviews.com
The scanner goes through an FTP server to disguise the source. But this shouldnt come as a surprise. A port scan is an attack that sends client requests to a range of server port addresses on a host with the goal of finding an active port and exploiting a known vulnerability of that service. The response could be open closed and filtered or blocked. The idea is to probe as many listeners as possible and keep track of the ones that are. -p0- asks Nmap to scan every possible TCP port -v asks Nmap to be verbose about it -A enables aggressive tests such as remote OS detection serviceversion detection and the Nmap Scripting Engine NSE.
An example pattern of attack would appear in a web request log with strings like the following.
Scanning as a method for discovering exploitable communication channels has been around for ages. There are numerous port scanning tools and popular examples are Nmap and Super Scan. But this shouldnt come as a surprise. Most port scanners only scan TCP ports. The probe elicits different responses from the target system depending. Network and security administrators use scanning to test firewall rules for example.
 Source: researchgate.net
Source: researchgate.net
These versions of SSL are affected by several cryptographic. A port scan would tell an attacker which ports are open on the system and that would help them formulate a plan of attack. Network and security administrators use scanning to test firewall rules for example. Hacker scans the network for specific information based on the information gathered during reconnaissance. We can control likewise from which local port will begin the scan 5050.

This method includes the use of dialers port scanners and other data-gathering equipment. An example pattern of attack would appear in a web request log with strings like the following. The remote service accepts connections encrypted using SSL 20 andor SSL 30. Ports the scan explores. The idea is to probe as many listeners as possible and keep track of the ones that are.
 Source: computertechreviews.com
Source: computertechreviews.com
Scanning as a method for discovering exploitable communication channels has been around for ages. A filtered or blocked response means the port is neither active nor inactive. Port scanning is a legitimate tool. Preventing a port scan attack is reliant on having effective updated threat intelligence that is in line with the evolving threat landscape. These versions of SSL are affected by several cryptographic.
 Source: datto.com
Source: datto.com
The activity of port scanning can be done as part of security assessment of ones own organization seeking to weed out security holes. For instance a port scanner will send a TCP SYN request to the host or range of hosts set to scan. For example if a Secure Shell SSH server was detected as listening on port 22 the attacker could try to connect and check for weak passwords. A decent feature from hping3 is that you can do a traceroute to a pointed out port viewing where your packet is blocked. An attacker performs an HTTP request against a target system which generates a log using Log4j 2 that leverages JNDI to perform a request to the attacker-controlled site.
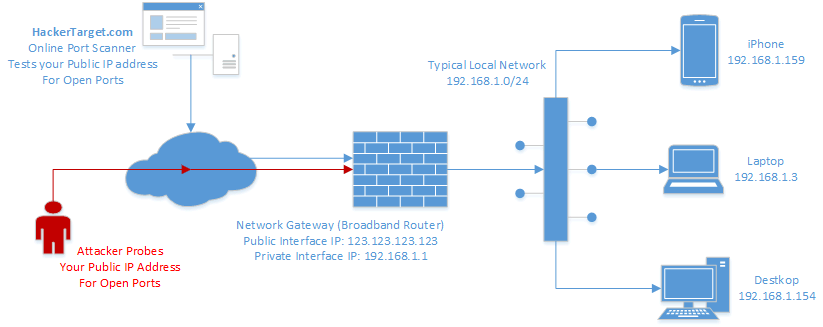 Source: windowsbulletin.com
Source: windowsbulletin.com
A filtered or blocked response means the port is neither active nor inactive. Network and security administrators use scanning to test firewall rules for example. An attacker performs an HTTP request against a target system which generates a log using Log4j 2 that leverages JNDI to perform a request to the attacker-controlled site. Scanning the target for weaknessesvulnerabilities. The activity of port scanning can be done as part of security assessment of ones own organization seeking to weed out security holes.
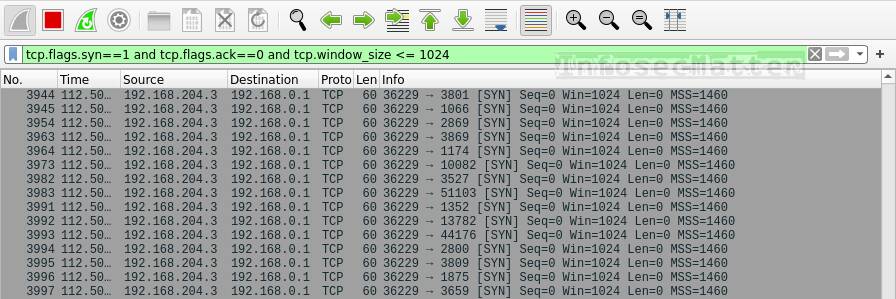 Source: infosecmatter.com
Source: infosecmatter.com
These cybercriminals can then determine your operations type of operating system and level of security. A port scan attack is just one classic example of a normal security technique being used against the very networks its designed to help protect. Network and security administrators use scanning to test firewall rules for example. This method includes the use of dialers port scanners and other data-gathering equipment. Scanning the target for weaknessesvulnerabilities.

Ports the scan explores. An attacker performs an HTTP request against a target system which generates a log using Log4j 2 that leverages JNDI to perform a request to the attacker-controlled site. A closed response means the port is inactive not listening and not responding. An example pattern of attack would appear in a web request log with strings like the following. The idea is to probe as many listeners as possible and keep track of the ones that are.
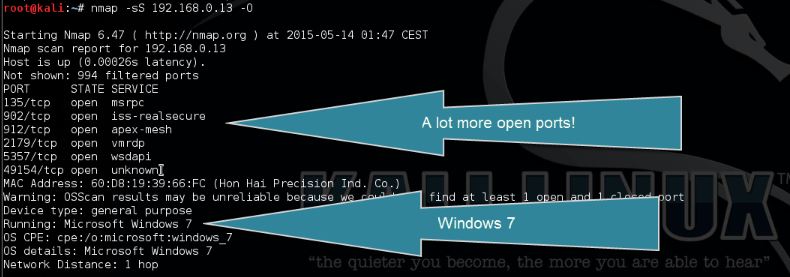 Source: hackingtutorials.org
Source: hackingtutorials.org
A filtered or blocked response means the port is neither active nor inactive. Hacker scans the network for specific information based on the information gathered during reconnaissance. An open response means that the port is active listening and responding. Traceroute to a determined port by Hping3. Most port scanners only scan TCP ports.
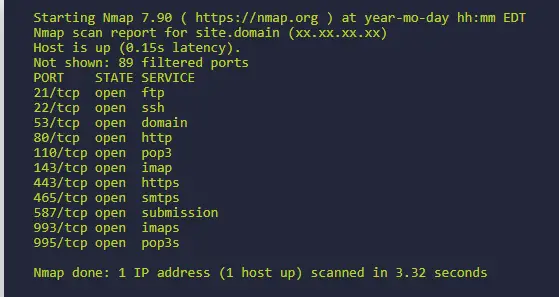 Source: nmap.online
Source: nmap.online
A filtered or blocked response means the port is neither active nor inactive. For example if a Secure Shell SSH server was detected as listening on port 22 the attacker could try to connect and check for weak passwords. Here hping3 will send a SYN packet to a tagged port 80 in our example. Port scan attacks generally require the attacker to send some kind of probe packet. The idea is to probe as many listeners as possible and keep track of the ones that are.
 Source: resources.infosecinstitute.com
Source: resources.infosecinstitute.com
The response could be open closed and filtered or blocked. The scanner looks for open UDP ports. It can simply be carried. User Datagram Protocol UDP. The activity of port scanning can be done as part of security assessment of ones own organization seeking to weed out security holes.
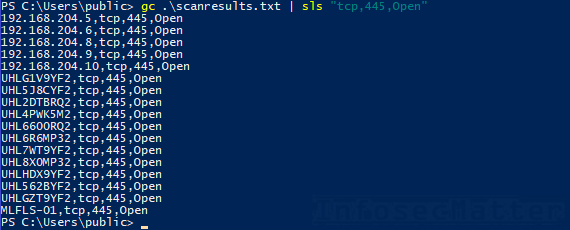 Source: infosecmatter.com
Source: infosecmatter.com
Naively executed this scan is among the easiest to detect because only local single-host detection mechanisms are required. There are numerous port scanning tools and popular examples are Nmap and Super Scan. The response could be open closed and filtered or blocked. Attacks like SUNBURST can use network scanning to get the lay of the land early on in the attack. An open response means that the port is active listening and responding.
 Source: stackoverflow.com
Source: stackoverflow.com
For example if a Secure Shell SSH server was detected as listening on port 22 the attacker could try to connect and check for weak passwords. The probe elicits different responses from the target system depending. A port scan attack is just one classic example of a normal security technique being used against the very networks its designed to help protect. For example open and closed responses will alert hackers that your network is in fact on the receiving end of the scan. Scanning the target for weaknessesvulnerabilities.
 Source: blogs.keysight.com
Source: blogs.keysight.com
The scanner pings the same port across more than one machine to see which computers are active. For instance a port scanner will send a TCP SYN request to the host or range of hosts set to scan. The remote service accepts connections encrypted using SSL 20 andor SSL 30. There are three types of responses to a port scan attack. The idea is to probe as many listeners as possible and keep track of the ones that are.
 Source: windowsbulletin.com
Source: windowsbulletin.com
Port scanning is one of the most popular techniques a hacker can use to discover services that can be compromised. Naively executed this scan is among the easiest to detect because only local single-host detection mechanisms are required. 31 Vertical Scans The vertical scan is a port scan that targets several destination ports on a single host. It can simply be carried. Scanning For Open Port by Hping3.
 Source: researchgate.net
Source: researchgate.net
There are numerous port scanning tools and popular examples are Nmap and Super Scan. A closed response means the port is inactive not listening and not responding. Traceroute to a determined port by Hping3. There are numerous port scanning tools and popular examples are Nmap and Super Scan. But this shouldnt come as a surprise.
 Source: cyberciti.biz
Source: cyberciti.biz
These versions of SSL are affected by several cryptographic. A port scan would tell an attacker which ports are open on the system and that would help them formulate a plan of attack. The scanner pings the same port across more than one machine to see which computers are active. Finally -T4 enables a more aggressive timing policy to speed up the scan. Attackers probe networks and systems to see how each port will react whether its open closed or filtered.
 Source: researchgate.net
Source: researchgate.net
An example pattern of attack would appear in a web request log with strings like the following. Scanning For Open Port by Hping3. The scanner pings the same port across more than one machine to see which computers are active. The remote service accepts connections encrypted using SSL 20 andor SSL 30. For example if a Secure Shell SSH server was detected as listening on port 22 the attacker could try to connect and check for weak passwords.

The scanner goes through an FTP server to disguise the source. Network and security administrators use scanning to test firewall rules for example. Scanning as a method for discovering exploitable communication channels has been around for ages. A decent feature from hping3 is that you can do a traceroute to a pointed out port viewing where your packet is blocked. Here hping3 will send a SYN packet to a tagged port 80 in our example.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title port scanning attack examples by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






