Your Port scanning attack prevention images are ready in this website. Port scanning attack prevention are a topic that is being searched for and liked by netizens today. You can Download the Port scanning attack prevention files here. Download all royalty-free photos and vectors.
If you’re searching for port scanning attack prevention pictures information linked to the port scanning attack prevention topic, you have pay a visit to the ideal site. Our website frequently gives you hints for viewing the maximum quality video and picture content, please kindly hunt and find more enlightening video content and images that fit your interests.
Port Scanning Attack Prevention. Learn how to detect and defend against port scan attacks. Detection and Characterization of Port Scan Attack Page 1. There are several methods of performing TCP scans. Prevent port scan attacks.
 Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library From docs.fortinet.com
Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library From docs.fortinet.com
Restrict access to known IP addresses. Useful tools include IP scanning Nmap and Netcat. Enable IPS under Network Protection Intrusion Prevention click gray toggle so it turns green Configure the Global IPS Settings required Configure Attack Patterns optionalrecommended Configure Anti-DoSFlooding optional Enable Anti-Portscan optional. A port scan attack occurs when an attacker sends packets with different port numbers to scan available services. Detection and Characterization of Port Scan Attack Page 1. When a hacker probes your system with a port scan attack each port will react one of three ways.
Service and Port Scan.
Adversaries may attempt to get a listing of services running on remote hosts including those that may be vulnerable to remote software exploitation. In our code structure Brute Force attacks are prevented by going through four. In the wrong hands this info could be part of a larger malicious scheme. Endpoint actions can be limited by requiring. Detection and Characterization of Port Scan Attack Page 1. There is reinforcing the computers firewall.
 Source: thesecuritybuddy.com
Source: thesecuritybuddy.com
If someone selects the Disable Port Scan and DoS Protection check box on the WAN screen that disables the protection. What services are running Which users own the services. Unfortunately even a denied. Learn how to detect and defend against port scan attacks. There are several methods of performing TCP scans.
 Source: pinterest.com
Source: pinterest.com
Endpoint actions can be limited by requiring. Preventing a port scan attack is reliant on having effective updated threat intelligence that is in line with the evolving threat landscape. Businesses also require strong security software port scanning tools and security alerts that monitor ports and prevent malicious actors from reaching their network. Adversaries may attempt to get a listing of services running on remote hosts including those that may be vulnerable to remote software exploitation. Enable IPS under Network Protection Intrusion Prevention click gray toggle so it turns green Configure the Global IPS Settings required Configure Attack Patterns optionalrecommended Configure Anti-DoSFlooding optional Enable Anti-Portscan optional.
 Source: m-cacm.acm.org
Source: m-cacm.acm.org
PORT SCAN ATTACK PREVENTION PRACTICES Administrators must regularly recheck their systems for any security vulnerabilities. Restrict access to known IP addresses. Methods to acquire this information include port scans and vulnerability scans using tools that are brought onto a system. Enable IPS under Network Protection Intrusion Prevention click gray toggle so it turns green Configure the Global IPS Settings required Configure Attack Patterns optionalrecommended Configure Anti-DoSFlooding optional Enable Anti-Portscan optional. They are not magical hacking fairy dust.
 Source: concise-courses.com
Source: concise-courses.com
These scanners are often used by amateur hackers. Answer What are port scan attacks and how can they be prevented. Some scanning tools will not match a known pattern because they are either new or a skilled attacker has changed SIP fields to make them less detectable. A port scan attack occurs when an attacker sends packets with different port numbers to scan available services. If someone selects the Disable Port Scan and DoS Protection check box on the WAN screen that disables the protection.
 Source: thesecuritybuddy.com
Source: thesecuritybuddy.com
On the Microsoft 365 Defender portal go to Vulnerability management Dashboard Threat awareness then click View vulnerability details to see the consolidated view of organizational exposure to the Log4j 2 vulnerability for example CVE-2021-44228 dashboard as shown in the following screenshots on the device software and vulnerable component level. Attack Detection and Prevention User Guide for Security Devices. By default the router uses port scan and DoS protection it is enabled to help guard a network against those attacks that inhibit or stop network availability. By creating dynamic address lists for each relevant port and protocol. Learn how to detect and defend against port scan attacks.
 Source: docs.fortinet.com
Source: docs.fortinet.com
Unfortunately even a denied. SYN scans the most common form of TCP scanning involve establishing a half-open connection to the target port by sending a SYN packet and evaluating the response. Methods to acquire this information include port scans and vulnerability scans using tools that are brought onto a system. When the Port Scanning Prevention Filter is triggered it usually means that there is no process listening on the port which WFP by design will block for security reasons. The plugin you want for either firewall is called suricata and in the rulesets there is a category for scans that will detect port scans and block.
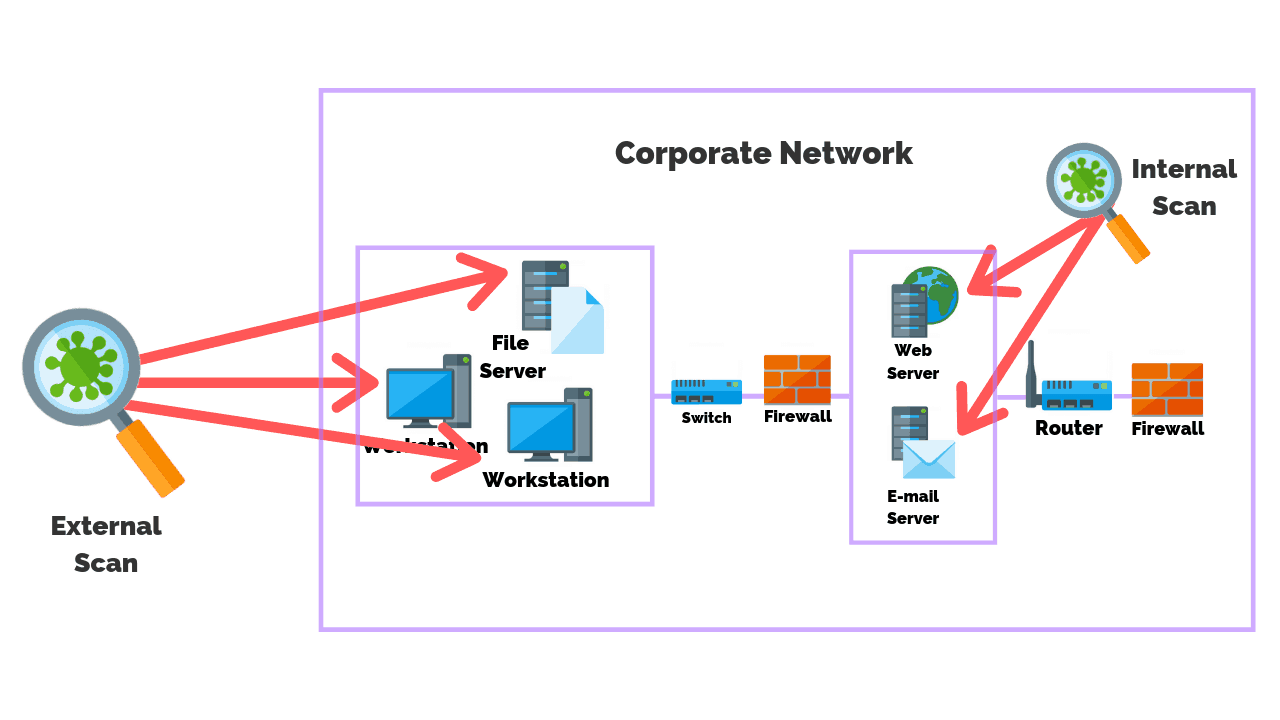 Source: purplesec.us
Source: purplesec.us
In the wrong hands this info could be part of a larger malicious scheme. Unfortunately even a denied. Port scanning is one of the most popular forms of reconnaissance ahead of a hack helping attackers determine which ports are most susceptible. Adversaries may attempt to get a listing of services running on remote hosts including those that may be vulnerable to remote software exploitation. This is because when a connection is attempted on a port where there is no listener WFP treats the packet as if it were coming from a Port Scanner and silently drops it.
 Source: m-cacm.acm.org
Source: m-cacm.acm.org
Port scan yourself to see your exposure. There are several methods of performing TCP scans. Use a firewall to prevent access to portsservices that should not be public. Endpoint actions can be limited by requiring. A denial of ser vice DoS attack prevents authorised and legitimate users from accessing computing or memory resource from the network b y.
 Source: m-cacm.acm.org
Source: m-cacm.acm.org
In our code structure Brute Force attacks are prevented by going through four. Preventing a port scan attack is reliant on having effective updated threat intelligence that is in line with the evolving threat landscape. There are several methods of performing TCP scans. Adversaries may attempt to get a listing of services running on remote hosts including those that may be vulnerable to remote software exploitation. Cases of a network breach should be promptly addressed to avoid further damages.
 Source: netsparker.com
Source: netsparker.com
Port scans provide data on how networks operate. Useful tools include IP scanning Nmap and Netcat. As previously mentioned TCP and UDP are frequently the protocols used in port scanning. There are several methods of performing TCP scans. Port scanning can lead to a hacker entering your network or stealing proprietary data.
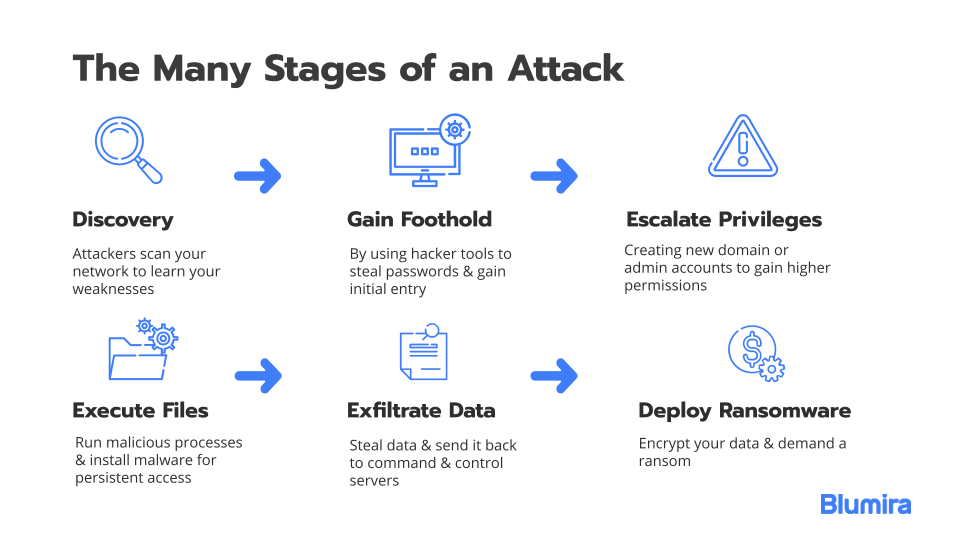 Source: blumira.com
Source: blumira.com
On the Microsoft 365 Defender portal go to Vulnerability management Dashboard Threat awareness then click View vulnerability details to see the consolidated view of organizational exposure to the Log4j 2 vulnerability for example CVE-2021-44228 dashboard as shown in the following screenshots on the device software and vulnerable component level. Port scanning can lead to a hacker entering your network or stealing proprietary data. Learn how to detect and defend against port scan attacks. Businesses also require strong security software port scanning tools and security alerts that monitor ports and prevent malicious actors from reaching their network. It plays a vital role by limiting the services allowed through it.
 Source: docs.fortinet.com
Source: docs.fortinet.com
Businesses also require strong security software port scanning tools and security alerts that monitor ports and prevent malicious actors from reaching their network. Attack Detection and Prevention User Guide for Security Devices. Port scanning is one of the most popular forms of reconnaissance ahead of a hack helping attackers determine which ports are most susceptible. For example if a remote host scans 10 ports in 0005 seconds equivalent to. Prevent port scan attacks.

The attack succeeds if a port responds. Service and Port Scan. Businesses also require strong security software port scanning tools and security alerts that monitor ports and prevent malicious actors from reaching their network. Scans are numerous and range from wasting resources to congesting the network to enabling future more serious attacks. DoSDDoS prevention settings can protect against attacks that cannot be identified by their SIP messaging.
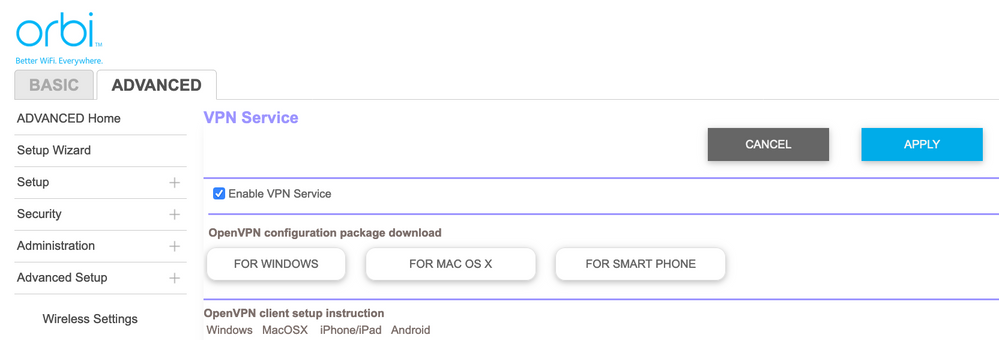
This is because when a connection is attempted on a port where there is no listener WFP treats the packet as if it were coming from a Port Scanner and silently drops it. Cases of a network breach should be promptly addressed to avoid further damages. Preventing a port scan attack is reliant on having effective updated threat intelligence that is in line with the evolving threat landscape. Having a firewall is imperative but one must also know the kinds of spoofing and deceitful techniques employed by hackers. They are not magical hacking fairy dust.
 Source: slidetodoc.com
Source: slidetodoc.com
On the Microsoft 365 Defender portal go to Vulnerability management Dashboard Threat awareness then click View vulnerability details to see the consolidated view of organizational exposure to the Log4j 2 vulnerability for example CVE-2021-44228 dashboard as shown in the following screenshots on the device software and vulnerable component level. What services are running Which users own the services. Detection and Characterization of Port Scan Attack Page 1. Attack Detection and Prevention User Guide for Security Devices. Port scanning provides the following information to attackers.
 Source: docs.fortinet.com
Source: docs.fortinet.com
Having a firewall is imperative but one must also know the kinds of spoofing and deceitful techniques employed by hackers. PORT SCAN ATTACK PREVENTION PRACTICES Administrators must regularly recheck their systems for any security vulnerabilities. Useful tools include IP scanning Nmap and Netcat. Port scanning is one of the most popular forms of reconnaissance ahead of a hack helping attackers determine which ports are most susceptible. SSH Telnet and Winbox ports to come with the Brute Force attacks on the Internet or local network will prevent future port scans.
 Source: slideplayer.com
Source: slideplayer.com
Within cloud environments adversaries may. When the Port Scanning Prevention Filter is triggered it usually means that there is no process listening on the port which WFP by design will block for security reasons. By default the router uses port scan and DoS protection it is enabled to help guard a network against those attacks that inhibit or stop network availability. Port scanning provides the following information to attackers. There is a plethora of tools that aim to determine a systems weaknesses and determine the best method for an attack.
 Source: itexamanswers.net
Source: itexamanswers.net
Heres how port scanning relates to these. Answer What are port scan attacks and how can they be prevented. Know what assets you have and what attackers will go for. In the wrong hands this info could be part of a larger malicious scheme. Port scanning can lead to a hacker entering your network or stealing proprietary data.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title port scanning attack prevention by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






